- Cybersecurity
Ransomware: Spot the Signs + How to Fight It

Jon Erdmann
Chief Information Technology Officer

What Is It?
Ransomware is a form of malware created and programmed to encrypt files on a device.
The fraudster will then turn around and demand ransom in exchange for decryption. They will threaten to release the information by selling or leaking it if they are not paid. The problem is, while they may ‘promise’ they will decrypt the information and won't leak anything if they're paid, there is no guarantee.
How Can You Prevent It?
- Keep your software updated.
- Enable strong spam filters.
- Turn off options to automatically download attachments.
- Watch for email red flags.
- Never click on links or open attachments that you are not expecting, regardless of who the sender is.
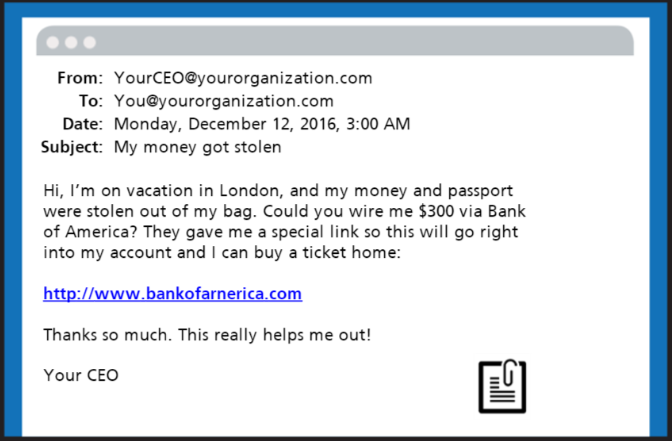
How to Spot Email Red Flags
- Sender Name
-
- Were you expecting an email from them?
- Is their name spelled correctly?
- Email Address
- Do they typically email you from this email address?
- Does it match your records?
- Context + Tone of Email
- Is there a sense of urgency or threat?
- What are they asking you to do?
- Are there spelling and/or grammar errors?
- What's Attached or Linked?
- Were you expecting them to send you an attachment or link?
- When you hover over the link, does the URL match where they say it's going?
- Does the file name make sense?
What to Do When It Happens
- Disconnect Affected Devices
- Immediately disconnect any compromised devices from the internet or network to prevent the malware from spreading further. This may involve disabling Wi-Fi or Ethernet connections on the affected device. Disconnecting shared drives and external storage devices can also help contain the infection.
- Seek Professional Help
- Contact a reputable cybersecurity expert or firm for assistance. Ransomware attacks can be complex, and attempting to resolve them without professional guidance can lead to further data loss or complications. Professionals can assess the situation, provide guidance on data recovery options, and help secure your devices and data to prevent future attacks. Additionally, report the attack to law enforcement agencies, as they may be able to assist in investigating the incident.
- Contact VISIONBank
- Contact VISIONBank immediately from an unaffected device if you have a ransomware attack so we can protect your accounts and prevent fraudulent activity from happening.